What is SOC

Security Orchestration, Automation, and Response (SOC) is a crucial component of modern cybersecurity, but the term SOC can also refer to a Security Operations Center. To clarify, let’s delve into the nuances of both definitions and explore their significance in the realm of cybersecurity.
Security Operations Center (SOC)
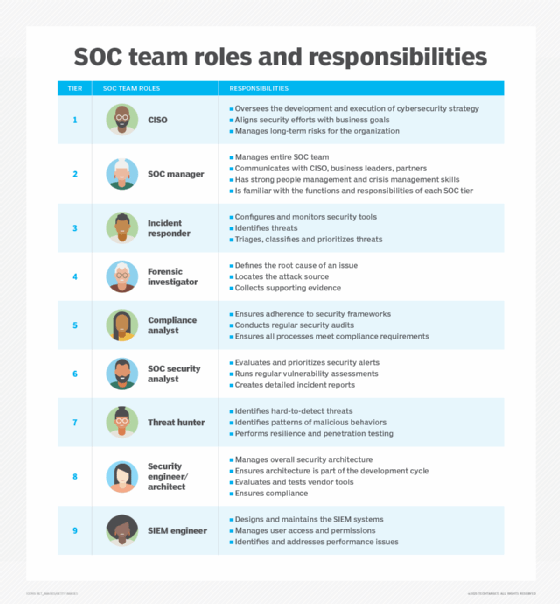
A Security Operations Center, often abbreviated as SOC, is a centralized unit that deals with security issues on an organizational and technical level. It’s essentially a team of experts, processes, and technology designed to monitor, detect, and respond to cybersecurity threats in real-time. The primary goal of a SOC is to provide a proactive and reactive approach to managing and mitigating IT risks.
Key components and functions of a SOC include:
- Incident Response: The process of responding to and managing security incidents. This involves detecting, containing, and eradicating threats, as well as post-incident activities to prevent future occurrences.
- Monitoring and Analysis: Continuous monitoring of the IT environment to identify potential security threats. This involves the use of various tools and technologies to analyze logs, network traffic, and system events.
- Vulnerability Management: Identifying and mitigating vulnerabilities in systems and applications. This includes conducting regular vulnerability assessments and applying patches or implementing other countermeasures as necessary.
- Compliance: Ensuring that the organization is compliant with relevant cybersecurity regulations and standards.
Security Orchestration, Automation, and Response (SOAR)
Security Orchestration, Automation, and Response (SOAR) refers to solutions that help automate and streamline security operations, particularly in the context of security incident response. SOAR integrates with various security tools and systems to automate workflows and improve the efficiency of security response processes.
Key features of SOAR solutions include:
- Orchestration: This involves linking different systems and processes to streamline security operations. It enables the integration of various security tools to automate response processes.
- Automation: Automating repetitive tasks and processes to reduce the workload on security teams. This can include tasks such as data collection, reporting, and initial response actions.
- Response: Enhancing the speed and effectiveness of response actions. SOAR solutions can automate the initial stages of incident response, such as isolating affected systems or blocking malicious traffic, allowing human analysts to focus on more complex aspects of incident response.
Conclusion
In the context of cybersecurity, SOC can refer to either a Security Operations Center, which is a team or facility dedicated to monitoring and responding to security threats, or to Security Orchestration, Automation, and Response (SOAR), which are solutions designed to automate and enhance the efficiency of security operations. Both concepts are crucial to an organization’s cybersecurity posture, as they help in detecting, responding to, and mitigating security threats effectively.
To implement an effective SOC or SOAR, organizations must consider their specific security needs, the nature of potential threats, and the necessity for continuous monitoring and improvement. This involves investing in the right technology, training skilled personnel, and adopting flexible and scalable strategies to address the evolving landscape of cybersecurity threats.
By understanding the roles and functions of both a Security Operations Center and SOAR solutions, organizations can better equip themselves to face the challenges of maintaining cybersecurity in today’s complex digital environment.
FAQs

What is the primary function of a Security Operations Center (SOC)?
+The primary function of a SOC is to monitor, detect, and respond to cybersecurity threats in real-time, providing a proactive and reactive approach to managing and mitigating IT risks.
How does Security Orchestration, Automation, and Response (SOAR) enhance security operations?
+SOAR solutions enhance security operations by automating and streamlining incident response processes, integrating with various security tools and systems to reduce the workload on security teams and improve response efficiency.
What are the key components of a Security Operations Center (SOC)?
+The key components include incident response, monitoring and analysis, vulnerability management, and compliance. These components work together to provide a comprehensive cybersecurity posture.
Recent Developments and Future Trends
The field of cybersecurity, including both SOCs and SOAR solutions, is rapidly evolving. Recent developments include the integration of Artificial Intelligence (AI) and Machine Learning (ML) into security operations to enhance threat detection and response. The use of cloud-based security services is also on the rise, offering scalability and flexibility to security operations.
Future trends will likely focus on further automation, the adoption of more advanced technologies such as blockchain for security, and a greater emphasis on human-machine collaboration to combat increasingly sophisticated cyber threats. The ability to adapt and evolve will be crucial for organizations looking to stay ahead of the curve in cybersecurity.
Conclusion
In conclusion, understanding the concepts of a Security Operations Center and Security Orchestration, Automation, and Response is vital for any organization aiming to enhance its cybersecurity posture. By leveraging these concepts and technologies, organizations can improve their ability to detect and respond to cyber threats, ultimately protecting their digital assets and ensuring the continuity of their operations. As the cybersecurity landscape continues to evolve, the importance of SOCs and SOAR will only continue to grow, making them essential components of modern cybersecurity strategies.