What is SIEM Security
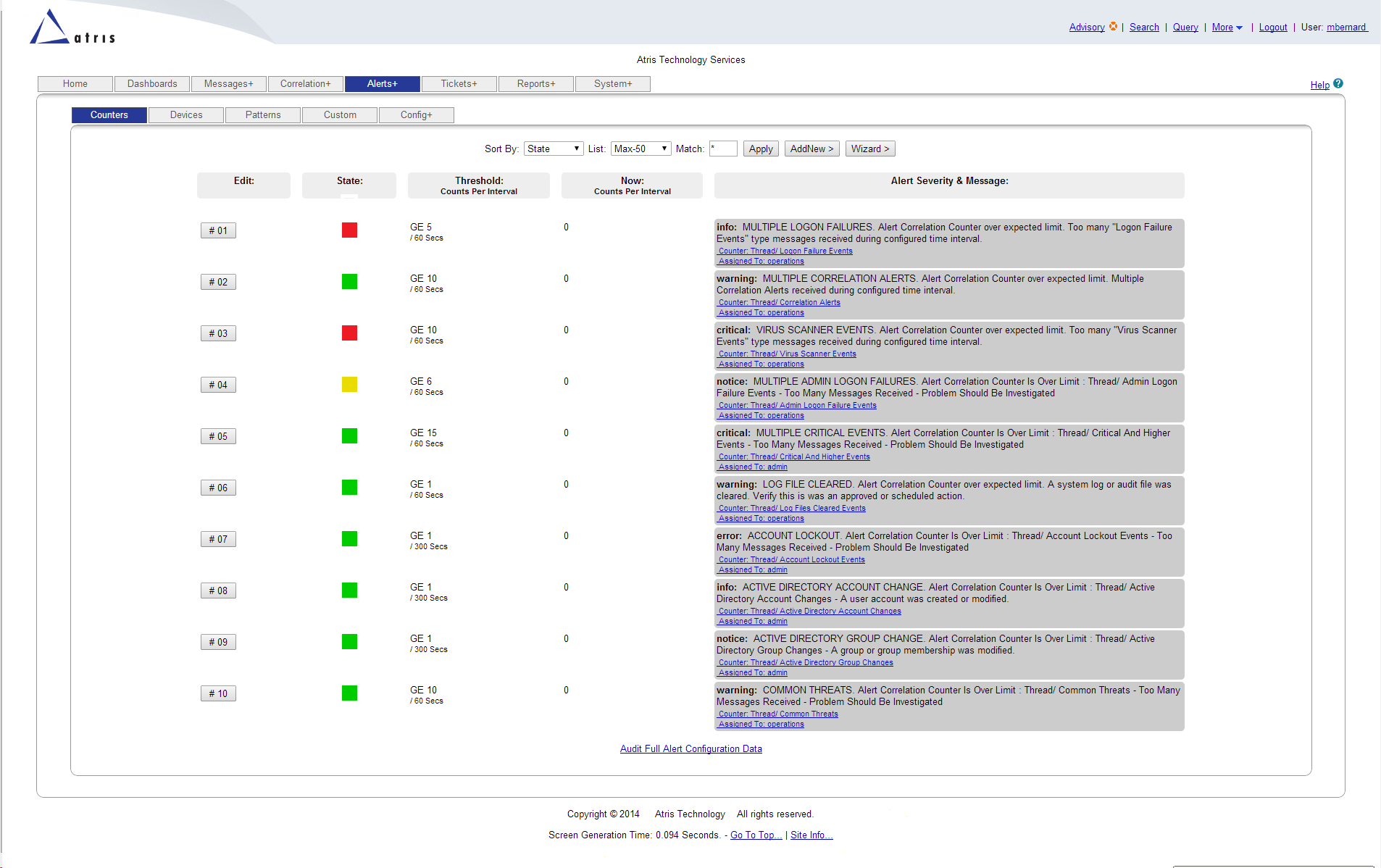
Security Information and Event Management (SIEM) systems are a crucial component of modern cybersecurity, serving as the backbone for threat detection, incident response, and compliance management. In essence, SIEM security is designed to provide real-time monitoring and analysis of security-related data from various sources, such as network devices, servers, and applications. This comprehensive overview aims to delve into the world of SIEM, exploring its definition, benefits, components, and the latest trends in this evolving field.
Definition and Functionality
A SIEM system collects, stores, and analyzes log data from an organization’s IT environment to identify potential security threats. By leveraging advanced analytics and machine learning algorithms, SIEM solutions can detect anomalies, pinpoint vulnerabilities, and alert security teams to respond promptly to emerging threats. The primary functions of a SIEM system include:
- Data Collection: Gathering log data from various sources across the network, including firewalls, intrusion detection systems, routers, and operating systems.
- Data Storage: Securing and managing the collected data in a centralized repository, ensuring compliance with regulatory requirements.
- Data Analysis: Applying sophisticated analytics to identify patterns, anomalies, and potential security threats in real-time.
- Alerting and Reporting: Notifying security personnel of detected threats and providing detailed reports for compliance and auditing purposes.
Benefits of SIEM Systems
Implementing a SIEM system offers numerous benefits to organizations seeking to bolster their cybersecurity posture:
- Enhanced Threat Detection: Identifies potential security threats in real-time, enabling swift response and mitigation.
- Compliance Management: Facilitates regulatory compliance by storing and analyzing log data, generating reports, and providing audit trails.
- Incident Response: Streamlines the incident response process by providing detailed insights into security incidents.
- Improved Security Posture: Offers a comprehensive view of the organization’s security landscape, enabling informed decision-making and strategic planning.
- Cost Savings: Automates manual security monitoring and analysis tasks, reducing the workload and associated costs.
Components of a SIEM System
A typical SIEM system consists of the following components:
- Data Collection Agents: Responsible for collecting log data from various sources and forwarding it to the SIEM server.
- SIEM Server: The central component that stores, analyzes, and correlates the collected data.
- Database: Stores the collected log data, providing a centralized repository for analysis and reporting.
- Analytics Engine: Applies advanced analytics and machine learning algorithms to detect anomalies and identify potential security threats.
- User Interface: Provides a graphical interface for security personnel to monitor, analyze, and respond to security incidents.
Latest Trends in SIEM
The SIEM market is evolving rapidly, driven by advances in technology and emerging threats. Some of the latest trends in SIEM include:
- Cloud-Based SIEM: Offers scalability, flexibility, and reduced costs, making it an attractive option for organizations.
- Artificial Intelligence (AI) and Machine Learning (ML): Enhances threat detection and incident response capabilities, enabling more effective security monitoring.
- Security Orchestration, Automation, and Response (SOAR): Integrates SIEM with other security tools, automating incident response and streamlining security operations.
- User and Entity Behavior Analytics (UEBA): Focuses on detecting insider threats and malicious activity by analyzing user and entity behavior.
Implementation and Best Practices
When implementing a SIEM system, consider the following best practices:
- Define Clear Goals and Objectives: Establish a clear understanding of the organization’s security requirements and objectives.
- Choose the Right SIEM Solution: Select a SIEM system that aligns with the organization’s size, complexity, and security needs.
- Configure and Tune the SIEM System: Customize the SIEM system to meet the organization’s specific requirements, optimizing its performance and effectiveness.
- Monitor and Analyze Logs: Regularly monitor and analyze log data to identify potential security threats and improve incident response.
- Continuously Update and Refine the SIEM System: Stay up-to-date with the latest security threats and trends, refining the SIEM system to ensure its continued effectiveness.
In conclusion, SIEM security is a vital component of modern cybersecurity, providing real-time monitoring, analysis, and incident response capabilities. By understanding the definition, benefits, components, and latest trends in SIEM, organizations can make informed decisions when selecting and implementing a SIEM system, ultimately enhancing their security posture and protecting against emerging threats.
Frequently Asked Questions
What is the primary function of a SIEM system?
+The primary function of a SIEM system is to collect, store, and analyze log data from various sources to identify potential security threats and detect anomalies in real-time.
What are the benefits of implementing a SIEM system?
+The benefits of implementing a SIEM system include enhanced threat detection, compliance management, improved incident response, and cost savings. Additionally, a SIEM system provides a comprehensive view of the organization’s security landscape, enabling informed decision-making and strategic planning.
What are the latest trends in SIEM?
+The latest trends in SIEM include cloud-based SIEM, artificial intelligence (AI) and machine learning (ML), security orchestration, automation, and response (SOAR), and user and entity behavior analytics (UEBA). These trends are driving the evolution of SIEM, enabling more effective security monitoring and incident response.
How do I choose the right SIEM solution for my organization?
+When choosing a SIEM solution, consider the organization’s size, complexity, and security needs. Evaluate the SIEM system’s scalability, flexibility, and customization options, as well as its ability to integrate with existing security tools and systems. Additionally, consider the vendor’s reputation, support, and pricing model.
What are the best practices for implementing a SIEM system?
+Best practices for implementing a SIEM system include defining clear goals and objectives, choosing the right SIEM solution, configuring and tuning the SIEM system, monitoring and analyzing logs, and continuously updating and refining the SIEM system. By following these best practices, organizations can ensure the effective deployment and operation of their SIEM system.



