Obfuscated Server Explained

The concept of an obfuscated server is a complex and multifaceted one, rooted in the realms of cybersecurity and network architecture. At its core, an obfuscated server refers to a server that has been intentionally configured to conceal its identity, location, or purpose from potential attackers, unauthorized users, or even law enforcement agencies. This is achieved through a variety of sophisticated techniques and technologies designed to obscure the server’s presence on the network, making it difficult to detect, track, or exploit.
One of the primary reasons for deploying an obfuscated server is to enhance security. By hiding the server’s identity and location, organizations can significantly reduce the risk of targeted attacks, such as distributed denial-of-service (DDoS) attacks or sophisticated hacking attempts. This is particularly important for high-stakes environments, such as financial institutions, government agencies, or entities handling sensitive data, where the confidentiality, integrity, and availability of information are paramount.
Techniques for Obfuscation
Several techniques are employed to obfuscate a server, each serving to complicate the process of detection or exploitation:
- Encryption: Utilizing advanced encryption protocols to encode all communication to and from the server, making it indecipherable to unauthorized parties.
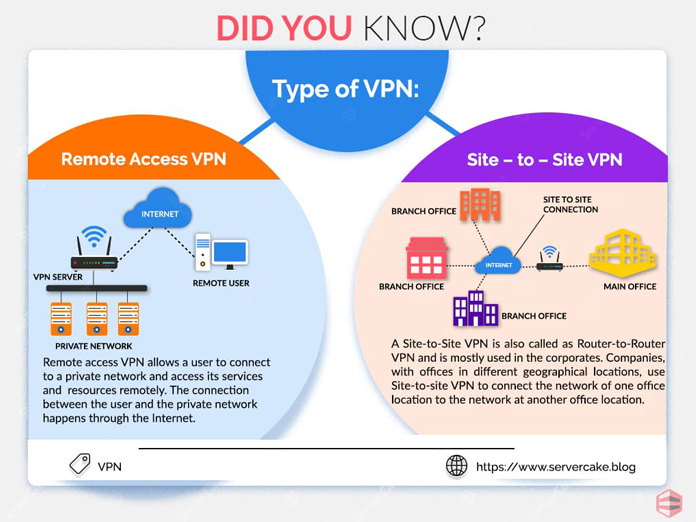
- Virtual Private Networks (VPNs): Implementing VPNs to mask the server’s IP address, making it appear as if the traffic is originating from a different location.
- Proxy Servers: Setting up proxy servers to act as intermediaries between the obfuscated server and the internet, further obscuring the server’s identity.
- Domain Name System (DNS) Manipulation: Using DNS servers that do not log queries or utilizing techniques like DNS over HTTPS (DoH) to conceal the server’s domain name resolution processes.
- Traffic Obfuscation: Modifying the patterns and characteristics of network traffic to make it blend in with regular internet traffic, avoiding raising suspicions.
Applications and Implications
The deployment of obfuscated servers spans various domains, each with its unique implications:
- Cybersecurity Research: Obfuscated servers are used in controlled environments to study and understand cyber threats without being detected by malicious actors.
- High-Security Data Storage: Organizations use obfuscated servers for storing sensitive data, ensuring that even if a breach occurs, the location and nature of the data remain obscure.
- Whistleblower Platforms: To protect the identity of whistleblowers, platforms may use obfuscated servers to receive and process tips without revealing the source.
- Secure Communication: Governments and military organizations may rely on obfuscated servers to facilitate secure communication that cannot be intercepted or traced back to its origin.
Challenges and Ethical Considerations
While obfuscated servers offer unparalleled security, they also present several challenges and raise ethical questions:
- Accessibility vs. Security: The trade-off between making a server highly secure through obfuscation and maintaining accessibility for authorized users.
- Legal Implications: The use of obfuscated servers can complicate legal investigations, as tracing and subscribing illegal activities becomes more challenging.
- Ethical Use: Ensuring that these servers are not used for illegal activities, such as hosting illicit content or facilitating cybercrime, while respecting privacy and security needs.
Future of Obfuscated Servers
As cybersecurity threats evolve, the technology and techniques behind obfuscated servers will continue to advance. The future may see more sophisticated methods of obfuscation, potentially leveraging artificial intelligence (AI) and machine learning (ML) to dynamically adapt to new threats. Moreover, there will be a growing need for international regulations and standards to ensure that obfuscated servers are used responsibly and ethically, balancing security with legal and ethical considerations.
In conclusion, obfuscated servers represent a pinnacle of cybersecurity efforts, offering a robust defense against an ever-threatening landscape of cyber threats. However, their use must be carefully managed to ensure that security enhancements do not come at the cost of ethical or legal compromises. As technology continues to evolve, the role and implementation of obfuscated servers will likely become even more critical in the protection of digital assets and sensitive information.
What are the primary benefits of using an obfuscated server?
+The primary benefits include enhanced security through obscurity, making it difficult for potential attackers to detect or exploit the server. This is particularly beneficial for high-security environments or entities handling sensitive data.
How do obfuscated servers impact cybersecurity research?
+Obfuscated servers play a crucial role in cybersecurity research by allowing for the study of cyber threats in a controlled environment without detection by malicious actors. This facilitates a deeper understanding of threats and the development of more effective countermeasures.
What are some of the ethical considerations surrounding the use of obfuscated servers?
+Key ethical considerations include ensuring that obfuscated servers are not used for illegal activities, respecting privacy, and balancing security needs with legal and ethical responsibilities. There's also a need for international cooperation to establish guidelines for their responsible use.
Implementing an Obfuscated Server: A Step-by-Step Guide

- Assessment of Needs: Determine the necessity of an obfuscated server based on the type of data or service being protected.
- Technique Selection: Choose the most appropriate obfuscation techniques based on the specific threats and requirements.
- Configuration and Deployment: Set up the obfuscated server, ensuring that all chosen techniques are properly implemented and tested.
- Monitoring and Maintenance: Regularly monitor the server's performance and update its configuration as necessary to counter new threats or adapt to changing needs.
- Evaluation of Effectiveness: Continuously assess the server's security posture and the effectiveness of the obfuscation techniques in place.
In navigating the complex world of obfuscated servers, understanding the nuances of their implementation, applications, and implications is crucial for both individuals and organizations seeking to enhance their cybersecurity posture. By embracing the latest technologies and best practices, while addressing the ethical and legal considerations, we can ensure that obfuscated servers serve as a robust defense against evolving cyber threats.