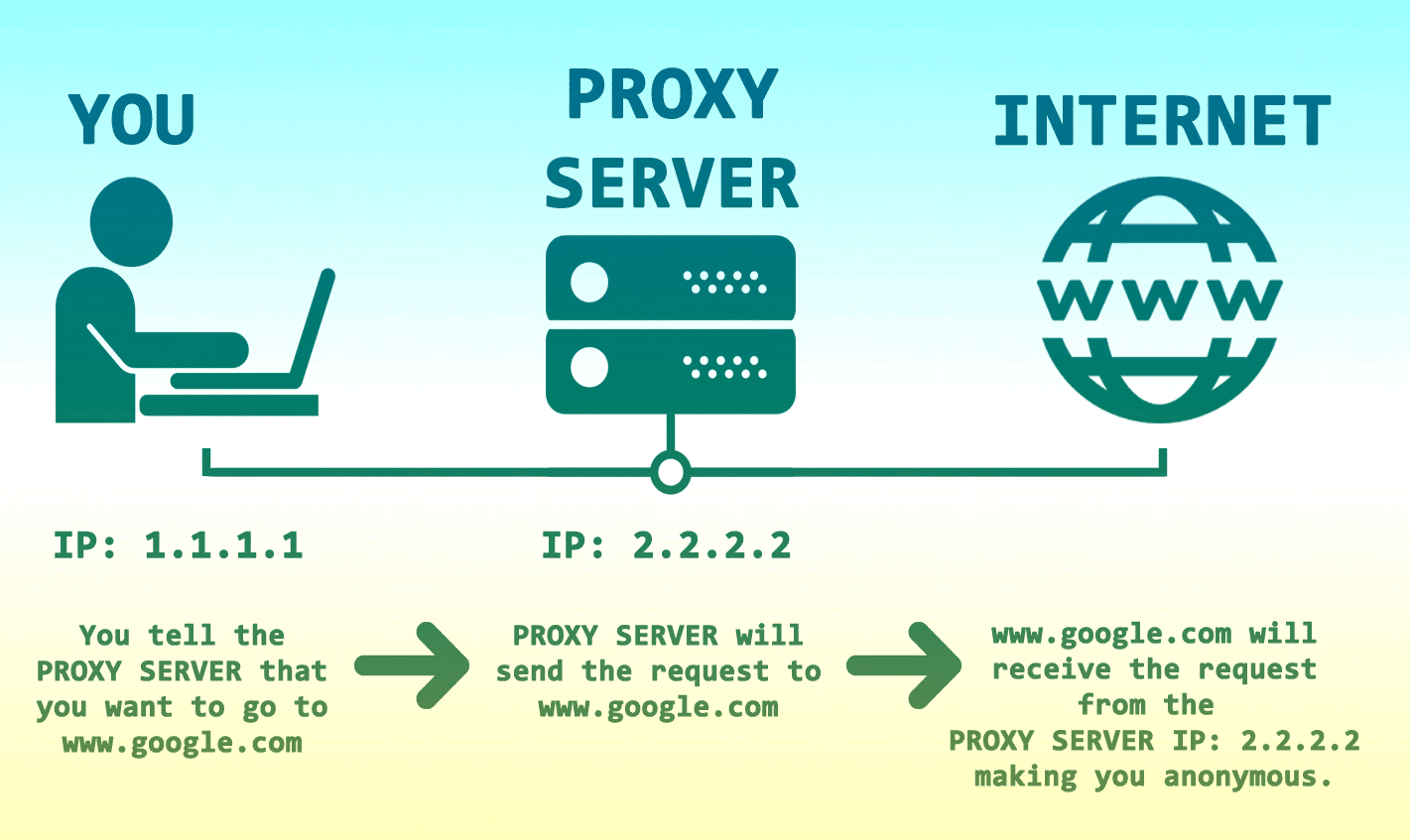
What is CASB

The Cloud Access Security Broker (CASB) is a critical component in the modern enterprise security architecture, designed to address the unique challenges posed by cloud services. As organizations increasingly adopt cloud-based applications and infrastructure, the need for a centralized platform to monitor, control, and secure cloud usage has become paramount. CASB solutions have emerged as a key technology to fill this gap, providing visibility, compliance, data security, and threat protection for cloud services.
Historical Evolution of CASB
The concept of CASB emerged in the early 2010s as a response to the rapid adoption of cloud services by enterprises. Initially, CASB focused primarily on providing visibility into cloud usage, identifying shadow IT, and ensuring compliance with regulatory requirements. Over time, the functionality of CASB solutions has expanded to include advanced security features such as data leakage prevention, malware detection, and encryption. Today, CASB is recognized as an indispensable tool for managing cloud security risks.
Core Functions of CASB
Visibility: CASB offers unparalleled visibility into cloud usage across the organization, helping IT teams understand which cloud services are being used, by whom, and how. This insight is crucial for identifying and mitigating potential security risks associated with unsanctioned cloud use.
Compliance: Ensuring compliance with regulatory requirements is a significant challenge in the cloud era. CASB solutions help organizations adhere to various compliance standards by providing features such as data encryption, access controls, and auditing capabilities.
Data Security: CASB protects sensitive data in cloud services through capabilities like data loss prevention (DLP), encryption, and tokenization. These features ensure that even if data is stored in or transmitted through cloud services, it remains secure and compliant with organizational policies.
Threat Protection: CASB solutions include advanced threat protection features to detect and prevent cyber threats targeting cloud services. This includes malware protection, intrusion detection, and incident response capabilities tailored for cloud environments.
Implementation and Deployment
CASB solutions can be deployed in various modes to suit different organizational needs. Common deployment models include:
- API-based: Integrates with cloud services via APIs to monitor and control cloud usage.
- Proxy-based: Acts as an intermediary for cloud traffic, providing real-time control and inspection.
- Agent-based: Utilizes agents installed on endpoints to monitor and secure cloud access.
Each deployment model has its advantages and is chosen based on the specific security, compliance, and infrastructure requirements of the organization.
Future Trends in CASB
As cloud computing continues to evolve, CASB solutions are adapting to meet new challenges. Emerging trends include:
- Integration with Other Security Tools: CASB is increasingly being integrated with other security tools and platforms, such as Security Information and Event Management (SIEM) systems and Security Orchestration, Automation, and Response (SOAR) solutions, to provide a unified security posture.
- Artificial Intelligence (AI) and Machine Learning (ML): The use of AI and ML in CASB solutions is becoming more prevalent, enabling more effective threat detection, predictive analytics, and automated response to security incidents.
- Cloud Security Posture Management (CSPM): CASB is expanding to include CSPM capabilities, which help organizations assess and remediate risks in their cloud infrastructure configurations.
Conclusion
In conclusion, CASB has become an essential security control for organizations leveraging cloud services. By providing comprehensive visibility, ensuring compliance, securing data, and protecting against threats, CASB solutions help mitigate the risks associated with cloud adoption. As cloud computing continues to evolve, the role of CASB in securing cloud environments will only continue to grow in importance.
What are the primary functions of a Cloud Access Security Broker (CASB)?
+The primary functions of a CASB include providing visibility into cloud usage, ensuring compliance with regulatory requirements, securing data in cloud services, and protecting against threats targeting cloud environments.
How does CASB help in securing cloud data?
+CASB secures cloud data through features such as data loss prevention (DLP), encryption, and tokenization, ensuring that data stored in or transmitted through cloud services remains secure and compliant with organizational policies.
What deployment models are available for CASB solutions?
+CASB solutions can be deployed in API-based, proxy-based, or agent-based models, each suited to different organizational needs and infrastructures.
In the realm of cloud security, staying informed about the latest developments and best practices is crucial. Whether you’re a seasoned security professional or just starting to explore the world of CASB, understanding its role in protecting cloud environments is essential for any organization aiming to securely leverage the benefits of cloud computing.