Warp Zero Trust Security
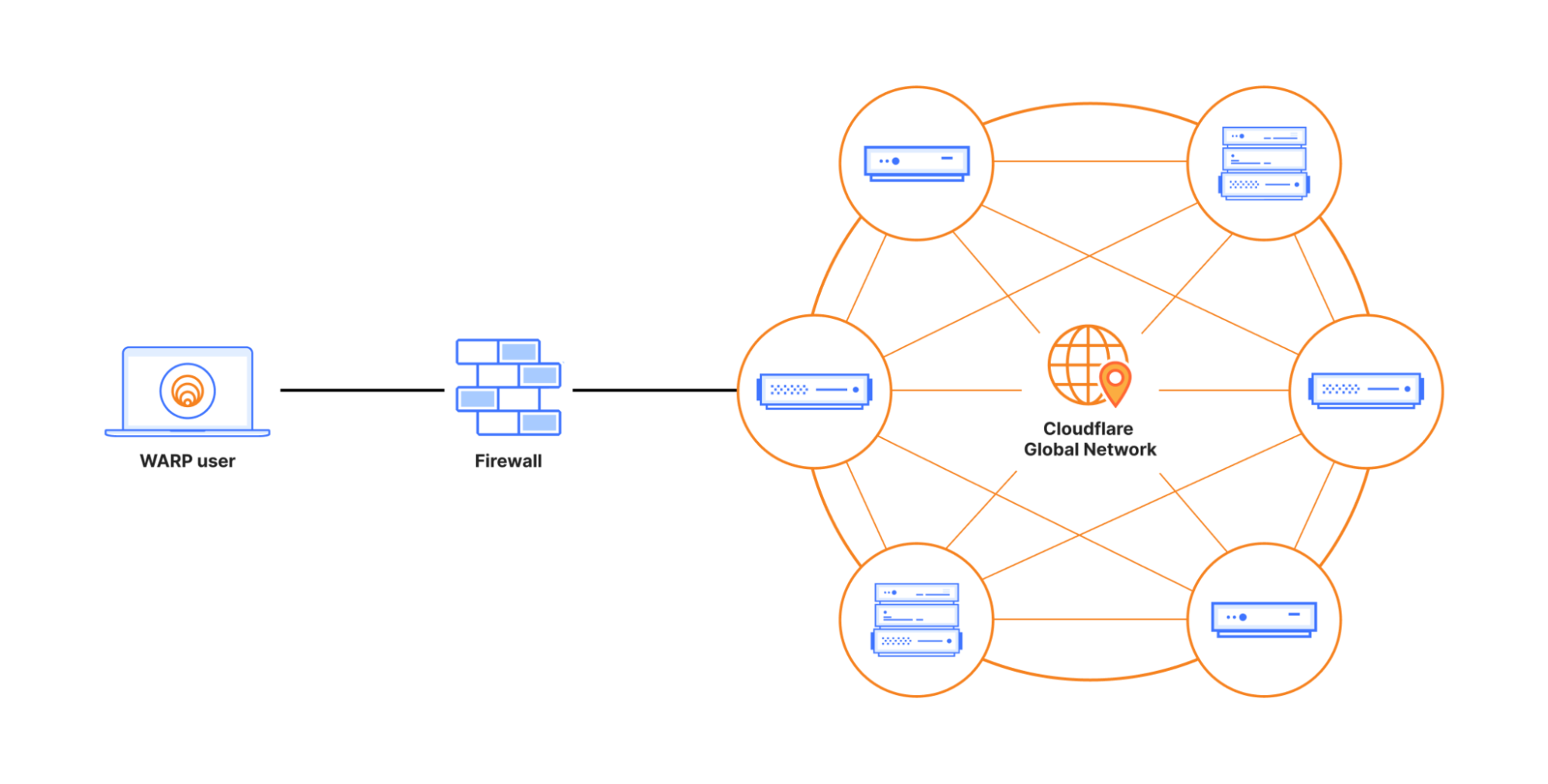
The concept of zero trust security has been gaining significant attention in recent years, and for good reason. Traditional security models have proven to be inadequate in protecting against the increasingly sophisticated threats that organizations face today. In this article, we will delve into the world of warp zero trust security, exploring its underlying principles, benefits, and implementation strategies.
At its core, zero trust security is based on the principle of “never trust, always verify.” This means that all users and devices, regardless of whether they are inside or outside the organization’s network, must be authenticated and authorized before being granted access to resources. This approach recognizes that threats can come from anywhere, and that the traditional perimeter-based security model is no longer effective.
Warp zero trust security takes this concept a step further by incorporating advanced technologies such as artificial intelligence, machine learning, and software-defined networking. These technologies enable organizations to create a highly dynamic and adaptive security environment that can respond to threats in real-time.
One of the key benefits of warp zero trust security is its ability to provide granular access control. By using advanced authentication and authorization protocols, organizations can ensure that users and devices only have access to the resources they need to perform their jobs, and nothing more. This approach also enables organizations to implement a least privilege access model, where users and devices are granted only the minimum level of access necessary to complete their tasks.
Another benefit of warp zero trust security is its ability to detect and respond to threats in real-time. By using advanced analytics and machine learning algorithms, organizations can identify potential threats and take action to prevent them from causing harm. This approach also enables organizations to implement a proactive security posture, where they can anticipate and prepare for potential threats before they occur.
Despite its many benefits, implementing warp zero trust security can be a complex and challenging process. Organizations must have a deep understanding of their network architecture, user behavior, and threat landscape in order to design and implement an effective zero trust security model. They must also have the necessary skills and resources to manage and maintain the system over time.
To overcome these challenges, organizations can take a phased approach to implementing warp zero trust security. This approach involves starting with a small pilot project and gradually expanding the scope of the implementation over time. Organizations can also work with experienced vendors and consultants to gain the necessary expertise and resources.
In terms of technology, there are several key components that are necessary for implementing warp zero trust security. These include:
- Advanced authentication protocols: Such as multi-factor authentication, behavioral biometrics, and device fingerprinting.
- Software-defined networking: Which enables organizations to create a highly dynamic and adaptive network environment.
- Artificial intelligence and machine learning: Which enable organizations to analyze user behavior and detect potential threats in real-time.
- Cloud-based security platforms: Which provide a scalable and flexible security infrastructure that can be easily integrated with existing systems.
Some of the key players in the warp zero trust security market include:
- Palo Alto Networks: Which offers a range of zero trust security solutions, including its Next-Generation Firewall and Prisma Access products.
- Cyberark: Which offers a range of privileged access management solutions, including its Core Privileged Access Security and Conjur products.
- Okta: Which offers a range of identity and access management solutions, including its Single Sign-On and Multi-Factor Authentication products.
In conclusion, warp zero trust security is a highly effective approach to protecting against the increasingly sophisticated threats that organizations face today. By incorporating advanced technologies such as artificial intelligence, machine learning, and software-defined networking, organizations can create a highly dynamic and adaptive security environment that can respond to threats in real-time.
What is warp zero trust security?
+Warp zero trust security is a highly effective approach to protecting against sophisticated threats. It involves authenticating and authorizing all users and devices, regardless of whether they are inside or outside the organization’s network.
What are the benefits of warp zero trust security?
+The benefits of warp zero trust security include its ability to provide granular access control, detect and respond to threats in real-time, and implement a proactive security posture.
How do I implement warp zero trust security?
+To implement warp zero trust security, organizations can follow a phased approach, starting with a small pilot project and gradually expanding the scope of the implementation over time. They can also work with experienced vendors and consultants to gain the necessary expertise and resources.



