Palo Alto Web Proxy Solution
The digital landscape of contemporary organizations is fraught with an array of cybersecurity challenges, from the proliferation of malicious software to the increasingly sophisticated techniques employed by hackers. Amidst this complex and ever-evolving threat environment, the role of a robust web proxy solution becomes paramount, not only for safeguarding against external threats but also for ensuring internal security and compliance. Among the array of solutions available, Palo Alto’s web proxy stands out, distinguished by its cutting-edge technology and comprehensive approach to cybersecurity.
The Evolution of Cyber Threats and Security Needs
The early days of the internet and the World Wide Web saw cybersecurity primarily as a concern related to viruses and basic malware. However, as technology has advanced, so too have the methods and tools used by malicious actors. Today, threats range from sophisticated phishing attacks and ransomware to advanced persistent threats (APTs) and zero-day attacks, which exploit previously unknown vulnerabilities. The rise of cloud computing, IoT devices, and remote work has further expanded the attack surface, making traditional perimeter-based security models less effective.
The Role of a Web Proxy in Cybersecurity
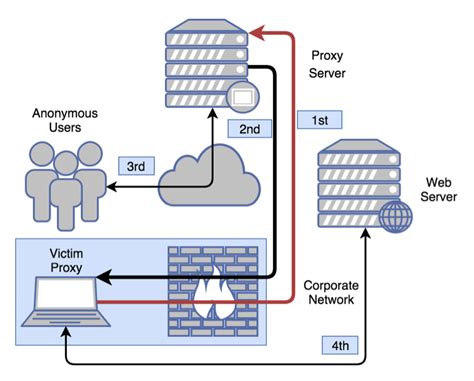
A web proxy server acts as an intermediary between a client (usually a user’s browser) and the internet. It can cache frequently accessed resources, filter out malicious content, and even monitor user activities. In the context of cybersecurity, a web proxy is invaluable for several reasons:
- Content Filtering: By blocking access to known malicious websites and filtering out harmful content, a web proxy can significantly reduce the risk of malware infections and other web-based threats.
- Anonymity and Privacy: A web proxy can mask the IP address of the client, enhancing privacy and making it more difficult for attackers to track users back to their internal network.
- Caching: By caching frequently accessed web pages, a web proxy can improve internet browsing speed and reduce the load on the external network connection, which can be particularly useful in scenarios where bandwidth is limited.
- Monitoring and Control: A web proxy can be configured to monitor and control user activity on the internet, enforcing company policies and preventing data leaks.
Palo Alto Web Proxy: Advanced Threat Protection
Palo Alto’s web proxy solution is part of its broader suite of security products, designed with the philosophy of prevention in mind. It integrates advanced threat protection capabilities with traditional web proxy features, making it a powerful tool against modern cyber threats. Key features include:
- Advanced URL Filtering: Palo Alto’s solution doesn’t just block known bad sites; it also uses advanced URL filtering to identify and block unknown malicious sites through analysis of URL characteristics.
- Threat Prevention: By leveraging Palo Alto’s threat intelligence, the web proxy can detect and block known threats, including zero-day threats, in real-time.
- SSL Decryption: To combat the growing trend of encrypted attacks, Palo Alto’s web proxy offers SSL decryption, allowing for the inspection of encrypted traffic for threats without compromising performance.
- User Identification: The solution integrates with various authentication systems, enabling user-based policies that can enforce role-based access control and monitor user activity on the internet.
Implementation and Management
Implementing a Palo Alto web proxy involves several steps, starting from planning and deployment to ongoing management and optimization. The process can be complex, especially in large, distributed environments. However, Palo Alto provides a range of tools and resources to simplify this process:
- Centralized Management: Palo Alto’s management platform allows administrators to manage their web proxy deployment from a single console, simplifying policy creation, deployment, and monitoring.
- Integration with Existing Infrastructure: The solution is designed to integrate seamlessly with existing security infrastructure, including firewalls, intrusion detection systems, and security information and event management (SIEM) systems.
- Scalability: Whether you’re a small business or a large enterprise, Palo Alto’s web proxy can scale to meet your needs, supporting high-speed, low-latency performance even in the most demanding environments.
Future Trends in Web Proxy Solutions
As the cybersecurity landscape continues to evolve, web proxy solutions must adapt to address emerging threats and technologies. Some key areas of focus include:
- Cloud Integration: With more applications moving to the cloud, web proxy solutions need to seamlessly integrate with cloud environments, ensuring consistent security policies across on-premises and cloud-based applications.
- Artificial Intelligence (AI) and Machine Learning (ML): The incorporation of AI and ML technologies can enhance threat detection capabilities, enabling web proxies to better identify and respond to novel threats in real-time.
- Endpoint Security: Tighter integration with endpoint security solutions can provide comprehensive protection, from the user device to the internet, reducing the risk of threats bypassing traditional network security controls.
Conclusion
In conclusion, the Palo Alto web proxy solution represents a significant advancement in cybersecurity, leveraging advanced technologies to protect against the sophisticated threats of today and tomorrow. By understanding the evolving landscape of cyber threats and the critical role a web proxy plays in modern security architectures, organizations can better position themselves to face the challenges of the digital age. Whether through its robust threat prevention capabilities, advanced URL filtering, or seamless integration with existing infrastructure, Palo Alto’s web proxy is a powerful tool in the ongoing quest for cybersecurity.
What is the primary function of a web proxy in cybersecurity?
+The primary function of a web proxy in cybersecurity is to act as an intermediary between a client and the internet, providing content filtering, anonymity, caching, and monitoring and control capabilities to protect against web-based threats.
How does Palo Alto’s web proxy solution address advanced threats?
+Palo Alto’s web proxy solution addresses advanced threats through advanced URL filtering, threat prevention, SSL decryption, and user identification, leveraging its threat intelligence to detect and block known and unknown threats in real-time.
What future trends will shape the development of web proxy solutions?
+Future trends that will shape the development of web proxy solutions include cloud integration, the incorporation of artificial intelligence (AI) and machine learning (ML), and tighter integration with endpoint security solutions to provide comprehensive protection against evolving cyber threats.