OT SCADA Security Solutions
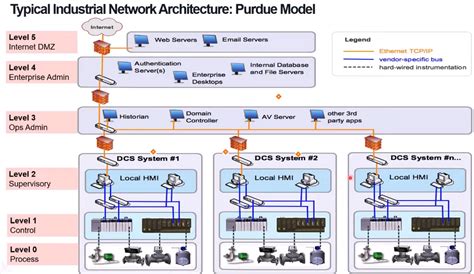
The convergence of operational technology (OT) and information technology (IT) has introduced a plethora of benefits, including increased efficiency, reduced costs, and enhanced productivity. However, this convergence has also created a significant challenge: the need for robust OT SCADA security solutions. SCADA (Supervisory Control and Data Acquisition) systems, which are critical components of OT, are now more vulnerable than ever to cyber threats. These threats can have devastating consequences, including disruptions to critical infrastructure, economic losses, and even loss of life.
To combat these threats, organizations must implement comprehensive OT SCADA security solutions that address the unique challenges of the OT environment. One of the primary challenges is the lack of standardization in OT systems, which can make it difficult to implement traditional IT security measures. For example, many OT systems use proprietary protocols and have limited support for standard security protocols such as SSL/TLS. Additionally, OT systems often have a longer lifespan than IT systems, which can make it difficult to keep them up-to-date with the latest security patches and updates.
Another challenge is the need for real-time monitoring and control in OT systems. SCADA systems, for instance, require immediate access to data and control functions to ensure the smooth operation of critical infrastructure. This real-time requirement can make it difficult to implement security measures that may introduce latency or disrupt the normal operation of the system. Furthermore, OT systems often have limited resources, such as processing power and memory, which can limit the implementation of resource-intensive security measures.
To address these challenges, organizations must adopt a holistic approach to OT SCADA security. This approach should include a combination of network security, endpoint security, and application security measures. Network security measures, such as firewalls and intrusion detection systems, can help prevent unauthorized access to OT systems. Endpoint security measures, such as antivirus software and host-based intrusion detection systems, can help prevent malware and other threats from compromising OT endpoints. Application security measures, such as secure coding practices and vulnerability management, can help prevent exploitation of vulnerabilities in OT applications.
In addition to these technical measures, organizations must also implement robust security policies and procedures. These policies and procedures should include incident response plans, security awareness training, and continuous monitoring and vulnerability assessment. Incident response plans can help ensure that organizations are prepared to respond quickly and effectively in the event of a security incident. Security awareness training can help ensure that personnel understand the importance of security and their role in maintaining it. Continuous monitoring and vulnerability assessment can help identify and remediate vulnerabilities before they can be exploited.
One of the most effective ways to implement OT SCADA security solutions is through the use of industrial control system (ICS) security frameworks. These frameworks provide a structured approach to security, including guidelines for risk assessment, security planning, and incident response. For example, the NIST Cybersecurity Framework provides a comprehensive framework for managing cybersecurity risk in OT systems. The framework includes five core functions: identify, protect, detect, respond, and recover. Each function provides a set of guidelines and best practices for managing cybersecurity risk, from identifying and assessing risk to responding to and recovering from security incidents.
Another effective way to implement OT SCADA security solutions is through the use of security information and event management (SIEM) systems. SIEM systems provide real-time monitoring and analysis of security-related data, allowing organizations to quickly identify and respond to security threats. For example, a SIEM system can monitor network traffic and system logs to identify potential security threats, such as unauthorized access attempts or malware activity. The system can then provide alerts and notifications to security personnel, allowing them to respond quickly and effectively to the threat.
Challenges in Implementing OT SCADA Security Solutions
Implementing OT SCADA security solutions can be challenging, especially in legacy systems that were not designed with security in mind. One of the primary challenges is the lack of standardization in OT systems, which can make it difficult to implement traditional IT security measures. For example, many OT systems use proprietary protocols and have limited support for standard security protocols such as SSL/TLS. Additionally, OT systems often have a longer lifespan than IT systems, which can make it difficult to keep them up-to-date with the latest security patches and updates.
Another challenge is the need for real-time monitoring and control in OT systems. SCADA systems, for instance, require immediate access to data and control functions to ensure the smooth operation of critical infrastructure. This real-time requirement can make it difficult to implement security measures that may introduce latency or disrupt the normal operation of the system. Furthermore, OT systems often have limited resources, such as processing power and memory, which can limit the implementation of resource-intensive security measures.
To address these challenges, organizations must adopt a phased approach to implementing OT SCADA security solutions. This approach should include a thorough risk assessment, followed by the implementation of security measures that address the most critical vulnerabilities. The risk assessment should identify potential security threats and vulnerabilities, as well as the likelihood and potential impact of a security incident. The security measures should then be implemented in a prioritized manner, with the most critical measures implemented first.
Implementing OT SCADA security solutions requires a deep understanding of the unique challenges of the OT environment. Organizations must adopt a holistic approach that includes network security, endpoint security, and application security measures, as well as robust security policies and procedures. By using ICS security frameworks and SIEM systems, organizations can ensure the security and integrity of their OT systems, even in the face of increasingly sophisticated cyber threats.
Future of OT SCADA Security Solutions

The future of OT SCADA security solutions looks promising, with a growing recognition of the importance of security in the OT environment. As OT systems continue to evolve and become more interconnected, the need for robust security measures will only continue to grow. In response, organizations are investing heavily in OT SCADA security solutions, including the development of new security technologies and the implementation of existing ones.
One of the most promising areas of development is the use of artificial intelligence (AI) and machine learning (ML) in OT SCADA security solutions. AI and ML can help organizations detect and respond to security threats in real-time, reducing the risk of security incidents and minimizing their impact. For example, an AI-powered SIEM system can analyze network traffic and system logs to identify potential security threats, and then provide recommendations for remediation.
Another promising area of development is the use of cloud-based OT SCADA security solutions. Cloud-based solutions can provide organizations with greater flexibility and scalability, allowing them to quickly deploy and manage security measures across their OT systems. For example, a cloud-based SIEM system can provide real-time monitoring and analysis of security-related data, allowing organizations to quickly identify and respond to security threats.
The future of OT SCADA security solutions is promising, with a growing recognition of the importance of security in the OT environment. As OT systems continue to evolve and become more interconnected, the need for robust security measures will only continue to grow. Organizations must invest in OT SCADA security solutions, including the development of new security technologies and the implementation of existing ones, to ensure the security and integrity of their OT systems.
Conclusion
In conclusion, OT SCADA security solutions are critical to the security and integrity of OT systems. Organizations must adopt a holistic approach to security, including network security, endpoint security, and application security measures, as well as robust security policies and procedures. By using ICS security frameworks and SIEM systems, organizations can ensure the security and integrity of their OT systems, even in the face of increasingly sophisticated cyber threats. As OT systems continue to evolve and become more interconnected, the need for robust security measures will only continue to grow, making it essential for organizations to invest in OT SCADA security solutions.
What are the primary challenges in implementing OT SCADA security solutions?
+The primary challenges in implementing OT SCADA security solutions include the lack of standardization in OT systems, the need for real-time monitoring and control, and the limited resources available in OT systems.
What is the role of ICS security frameworks in implementing OT SCADA security solutions?
+ICS security frameworks provide a structured approach to security, including guidelines for risk assessment, security planning, and incident response. They help organizations ensure the security and integrity of their OT systems by providing a comprehensive framework for managing cybersecurity risk.
What is the future of OT SCADA security solutions?
+The future of OT SCADA security solutions looks promising, with a growing recognition of the importance of security in the OT environment. As OT systems continue to evolve and become more interconnected, the need for robust security measures will only continue to grow, making it essential for organizations to invest in OT SCADA security solutions.



