5 Ways Evasive Malware Works
Evasive malware has become a significant threat in the cybersecurity landscape, with its ability to bypass traditional security measures and remain undetected for extended periods. Understanding how evasive malware works is crucial for developing effective defense strategies. Here, we will delve into the mechanisms and techniques used by evasive malware, exploring five key ways it operates.
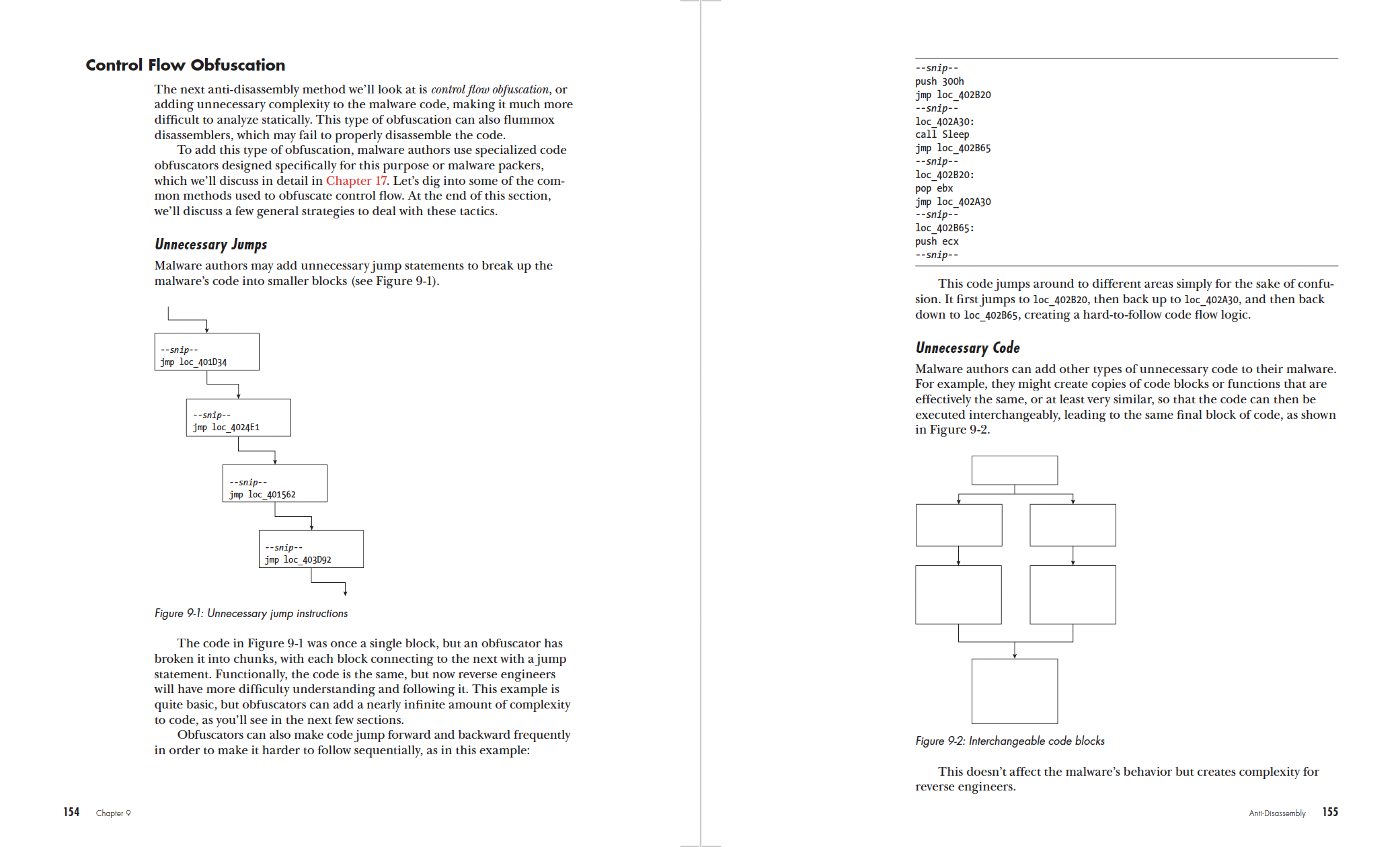
1. Code Obfuscation and Encryption
One of the primary methods evasive malware uses to avoid detection is code obfuscation and encryption. Obfuscation involves making the malware’s code difficult for humans and automated tools to understand, thereby hindering analysis efforts. This can be achieved through various techniques such as code packing, where the malware is compressed and encrypted, only to be unpacked in memory at runtime. Encryption takes it a step further by protecting the code from being reverse-engineered, as it can only be deciphered with the correct decryption key. By encrypting its communication channels and code, evasive malware can hide its true intentions and actions from security software.
Code obfuscation and encryption are powerful tools in the arsenal of evasive malware, making it challenging for security analysts to dissect and understand the malware's behavior, intent, and mechanisms.
2. Dynamic Detection Evasion
Evasive malware often employs dynamic detection evasion techniques, designed to evade the static analysis performed by many antivirus solutions. This includes polymorphic code, which changes its form with each infection, making it difficult for signature-based detection systems to identify. Additionally, evasive malware can use anti-debugging and anti-emulation techniques to detect when it is being run in a sandbox environment or debugged by a researcher, altering its behavior to appear benign or simply terminating to avoid detection.
| Technique | Description |
|---|---|
| Polymorphic Code | Changes its form with each infection, complicating signature-based detection. |
| Anti-Debugging | Detects and prevents debugging by security analysts. |
| Anti-Emulation | Identifies and evades sandbox environments used for malware analysis. |

3. Exploitation of Zero-Day Vulnerabilities
Evasive malware frequently exploits zero-day vulnerabilities—previously unknown weaknesses in software that have not been patched by the vendor. Since these vulnerabilities are not publicly known, there are no existing patches or signatures that can detect and block the exploit. This allows evasive malware to infect systems without being detected by traditional security software that relies on known signatures or patches. The use of zero-day exploits is particularly dangerous, as it gives the attackers a window of opportunity to execute their malicious code before any defensive measures can be taken.
Step 1: Identification of a zero-day vulnerability in widely used software.
Step 2: Development of an exploit to leverage this vulnerability for malicious entry.
Step 3: Execution of the exploit, gaining unauthorized access to targeted systems.
4. Social Engineering Tactics
Another approach used by evasive malware involves social engineering, where the malware relies on manipulating individuals into performing certain actions that compromise the security of their system. This can be through phishing emails, infected attachments, or even fake updates that appear legitimate. Once the user inadvertently executes the malware, it can bypass many security controls since it is the user themselves who initiated the action. Social engineering tactics are particularly effective because they exploit human psychology rather than technical vulnerabilities, making them harder to defend against with technology alone.
Social engineering is a powerful vector for evasive malware, as it exploits the weakest link in the security chain: human behavior and trust.
5. Fileless Malware and Living Off the Land (LOTL)
Lastly, evasive malware may adopt a fileless approach, residing solely in memory and leveraging existing system tools and applications to carry out malicious activities. This technique, known as Living Off the Land (LOTL), makes it extremely difficult for security software to detect the malware, as there are no malicious files written to disk and no unusual processes are launched. Instead, the malware manipulates legitimate system tools to perform its malicious tasks, blending in with normal system activity and evading detection.
Advantages for Malware Authors: Increased stealth, difficulty in detection, and the ability to operate under the radar of traditional security measures.
Challenges for Cybersecurity: Requires advanced detection methods beyond traditional signature-based systems, such as behavioral monitoring and anomaly detection.
Mitigation Strategies
To combat evasive malware effectively, organizations must adopt a multi-layered defense strategy that includes:
- Advanced Threat Protection (ATP) Solutions: Utilize solutions that can detect and mitigate threats in real-time, including those that have not been seen before.
- Employee Education: Regularly educate employees on how to identify and avoid social engineering attempts.
- Continuous Updates and Patching: Ensure all software is up-to-date with the latest security patches to minimize the risk of exploitation through known vulnerabilities.
- Network Segmentation: Implement network segmentation to limit the spread of malware in case of an infection.
- Incident Response Plans: Develop and regularly test incident response plans to quickly respond to and contain malware outbreaks.
What is the most effective way to protect against evasive malware?
+A combination of advanced threat protection solutions, regular software updates, employee education, and a robust incident response plan offers the best defense against evasive malware.
How does evasive malware exploit systems?
+Evasive malware exploits systems through various methods, including code obfuscation, dynamic detection evasion, exploitation of zero-day vulnerabilities, social engineering, and fileless malware techniques.
In conclusion, evasive malware presents a complex and evolving threat landscape that demands proactive, multi-faceted defense strategies. By understanding the mechanisms and techniques used by evasive malware, cybersecurity professionals can better equip themselves to combat these sophisticated threats, protecting both individuals and organizations from falling prey to these advanced attacks.