5 Tips Endpoint Protection
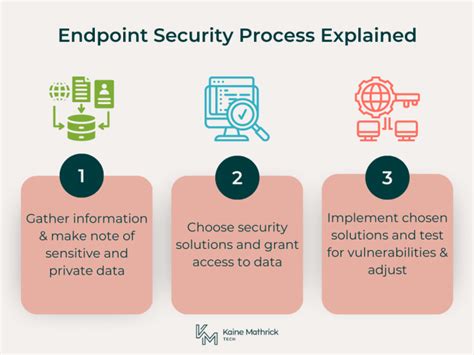
In today’s digital landscape, endpoint protection has become a critical component of any organization’s cybersecurity strategy. With the proliferation of remote work and the increasing sophistication of cyber threats, it’s essential to ensure that all devices connecting to your network are secure and up-to-date. Here are five tips to enhance your endpoint protection:
1. Implement a Comprehensive Endpoint Detection and Response (EDR) Solution
A robust EDR solution is the backbone of modern endpoint protection. It goes beyond traditional antivirus software by providing real-time monitoring and detection of threats, as well as the ability to respond to and remediate incidents swiftly. EDR solutions use advanced analytics and machine learning to identify and block suspicious activity, reducing the risk of a successful attack. When selecting an EDR solution, consider its ability to integrate with your existing security infrastructure and its scalability to meet the growing needs of your organization.
2. Keep Your Operating Systems and Software Up-to-Date
Ensuring that all endpoint devices have the latest operating system (OS) and software patches is crucial. Cyber attackers often exploit known vulnerabilities in outdated software to gain entry into systems. Regular updates typically include security patches that fix these vulnerabilities, thereby reducing the attack surface. Implement a robust patch management strategy that automates the updating process as much as possible, while also considering the need for testing patches to avoid disrupting critical business applications.
3. Use Strong Authentication and Access Controls
Weak passwords and poor access controls can significantly compromise endpoint security. Implementing strong authentication measures such as multi-factor authentication (MFA) can greatly reduce the risk of unauthorized access to endpoint devices. MFA requires a user to provide two or more verification factors to gain access to a resource, making it much harder for attackers to succeed with phishing or password cracking attacks. Additionally, enforce the principle of least privilege, where users are granted the minimum levels of access necessary to perform their jobs, limiting the potential damage from a compromised account.
4. Educate Users on Security Best Practices
Despite the best technical controls, user behavior remains a significant risk factor in endpoint security. Educating users on security best practices can significantly reduce the risk of successful attacks. This includes training on how to identify and report phishing emails, the importance of using strong and unique passwords, and the dangers of using public Wi-Fi for sensitive activities without a VPN. Regular security awareness training should be a part of your overall endpoint protection strategy, empowering users to become a part of your defense mechanism rather than a vulnerability.
5. Regularly Conduct Vulnerability Assessments and Penetration Testing
No security system is foolproof, and new vulnerabilities are continually discovered. Regular vulnerability assessments help identify weaknesses in your endpoint security posture, allowing you to address them before they can be exploited. Penetration testing (pen testing) takes this a step further by simulating cyber attacks on your endpoints to test their defenses. This proactive approach enables you to identify and fix potential entry points that an attacker could use, strengthening your overall endpoint protection and reducing the risk of a successful breach.
Implementing these strategies requires a comprehensive understanding of your endpoint landscape and the threats it faces. Continuous monitoring and adaptation are key to maintaining effective endpoint protection in a rapidly evolving cybersecurity environment.
Conclusion
Endpoint protection is not a set-it-and-forget-it proposition. It requires continuous effort, monitoring, and adaptation to stay ahead of emerging threats. By implementing a comprehensive EDR solution, keeping your systems up-to-date, using strong authentication, educating your users, and regularly assessing your vulnerabilities, you can significantly enhance your endpoint security posture. Remember, endpoint security is a critical component of your overall cybersecurity strategy, and investing in it is investing in the protection of your organization’s most valuable assets.
What is the primary benefit of using an Endpoint Detection and Response (EDR) solution?
+The primary benefit of an EDR solution is its ability to provide real-time monitoring and detection of threats, along with the capability to respond to and remediate incidents swiftly, thereby reducing the risk of a successful attack.
Why is keeping operating systems and software up-to-date important for endpoint security?
+Keeping systems up-to-date is crucial because it fixes known vulnerabilities that cyber attackers could exploit. Regular updates include security patches that reduce the attack surface, making it harder for attackers to gain entry into your systems.
How does multi-factor authentication (MFA) enhance endpoint security?
+MFA enhances endpoint security by requiring users to provide two or more verification factors to gain access, making it much harder for attackers to succeed with phishing or password cracking attacks, thereby protecting against unauthorized access.


